Example reverse proxy / TURN server deployment: single NIC on public address
Here is an example deployment where the reverse proxy and the TURN server application have been deployed with a single NIC on a public address.
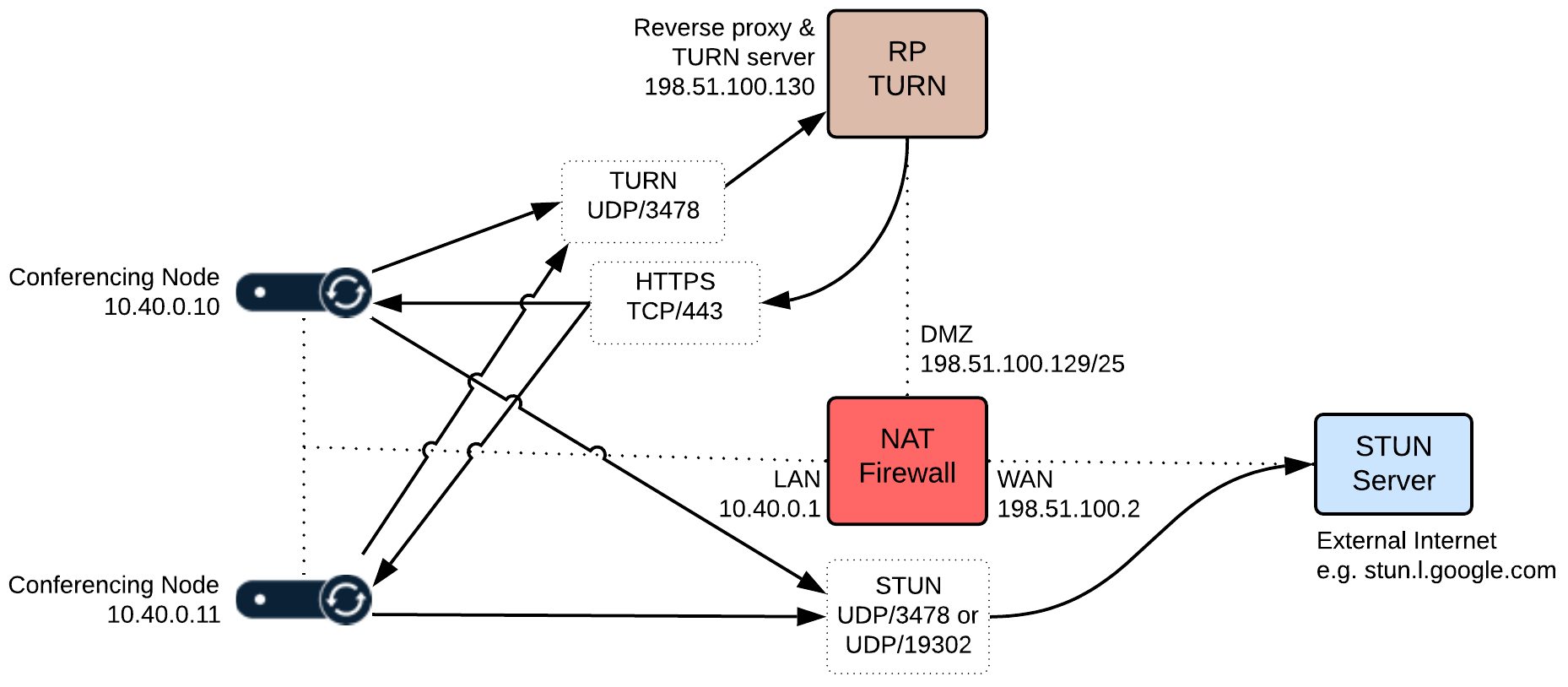
The environment is split into two parts — an internal, private network segment and a DMZ network. The private network has two Pexip Infinity Conferencing Nodes, while the DMZ perimeter network contains the reverse proxy and TURN server.
Note that all IP addresses in this guide are examples only — actual IP addressing is deployment specific.
- Two Conferencing Nodes have been deployed in the LAN segment with IP addresses 10.40.0.10 and 10.40.0.11.
- The firewall in this scenario has three network interfaces:
- LAN: 10.40.0.1/24
- DMZ: 198.51.100.129/25
- WAN: 198.51.100.2
- The DMZ network (198.51.100.129/25) can route network traffic to the LAN network (no NAT between LAN and DMZ).
- The reverse proxy and TURN server have been deployed in the DMZ subnet with IP address 198.51.100.130.
- As there is no NAT between the Conferencing Nodes in the LAN and the TURN server in the DMZ, the Conferencing Nodes have been configured to send their STUN requests to a STUN server in the public internet.
-
The firewall has been configured to allow:
- the reverse proxy to initiate HTTPS connections towards the Conferencing Node IP addresses
- Conferencing Nodes to send TURN packets to the TURN server on UDP port 3478
- Conferencing Nodes to send STUN packets to the STUN server, typically on UDP port 3478, although stun.l.google.com uses port 19302.
Example deployment used in this guide: single NIC on public address