Managing administrator access via LDAP
You can configure the Pexip Infinity platform to authenticate and authorize administrator login accounts via a centrally managed LDAP-accessible server. Integration with LDAP provides increased security, better auditing of changes, and more control and flexibility as you can assign different privileges to specific groups of users.
By default, Pexip Infinity only has a single local administrator account. Integration with an LDAP directory service allows multiple users to administer the platform. These users log in with their directory credentials, which is generally a Windows AD domain. When using LDAP:
- Instead of authenticating the supplied username and password credentials against its own internal database, Pexip Infinity contacts the LDAP server to authenticate the administrator's user account.
- It uses the account's LDAP group attributes in combination with role mappings defined in Pexip Infinity to determine which Pexip Infinity features the administrator is authorized to access.
- Every management API request is preceded by an authentication request to the LDAP server. If the frequency of API requests in your environment means that this is causing a significant load on your LDAP server, you may wish to consider using OAuth2 as an alternative authentication method for the management API. (The LDAP server will still receive requests for Administrator interface authentication.)
You can also enable client certificate authentication when using LDAP.
The configuration described here applies to all administrator accounts connecting to the Pexip Infinity Administrator interface or the Pexip Infinity management API. It does not apply to SSH connections. When using LDAP authentication, Pexip Infinity is configured by default to work with a Windows Active Directory LDAP server, but it can also be configured to work with other LDAP-accessible databases.
In addition to LDAP, you can authenticate and authorize administrator accounts connecting to the Pexip Infinity Administrator interface using Open ID Connect. For more information, see Managing administrator access via OIDC.
You can also allow administrator accounts connecting to the Pexip Infinity management API to use OAuth instead of, or in addition to, LDAP. For more information, see Managing API access via OAuth2.
The following sections describe:
- Configuration summary for LDAP authentication
- Configuring Pexip Infinity
- Configuring administrator roles
- Configuring role mappings
- Examples: configuring permissions for an AD group
- Reinstating the local admin account
Configuration summary for LDAP authentication
To enable authentication and authorization via LDAP, you need to configure both the LDAP database (if it is not already configured with user details) and the Pexip Infinity platform.
The LDAP database must be configured with:
- administrators' user credentials
- groups that define the capabilities of the users.
The Pexip Infinity platform must be configured with:
- an authentication source setting that uses an LDAP database
- connection details for the LDAP server; if the server address is an FQDN, ensure that it is resolvable over the DNS server configured for the Management Node
- administrator roles to control the actions that administrators can perform
- LDAP role mappings that map LDAP groups to administrator roles.
If a secure TLS connection between the LDAP server and the Management Node is required, ensure that:
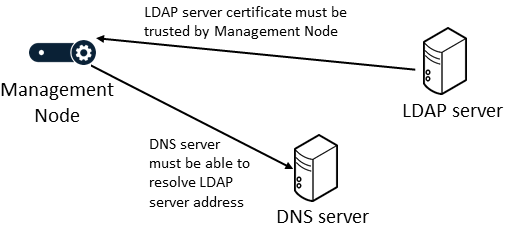
- The LDAP server address is specified as an FQDN (so that it matches the name on the certificate presented by the LDAP server, which is typically created for the host name rather than the IP address).
-
The Management Node trusts the certificate presented by the LDAP server; typically this means that the LDAP server certificate has to be uploaded to the Management Node as a trusted CA certificate (as the LDAP server's certificate is often generated by an internal authority which would not be included in Pexip's inbuilt list of trusted CA certificates).
Note that the Management Node's server certificate does not have to be trusted by the LDAP server (unless the LDAP server has been explicitly configured to demand a client certificate).
The Pexip Infinity platform configuration steps for specifying an LDAP authentication source, and configuring administrator and LDAP role mappings are described in more detail in the following sections, and there is an example that shows how to configure permissions for an AD group. For information about installing server and trusted CA certificates, see Managing TLS and trusted CA certificates.
Configuring Pexip Infinity
To allow administrators to use LDAP authentication when they log in to the Pexip Infinity Administrator interface or management API, go to . The options are:
| Option | Description |
|---|---|
| Authentication source |
The database to query for administrator authentication and authorization. Local database: uses the Pexip Infinity local on-box database. Administrators can only log in via the default account (typically admin) and will have full administrator privileges. LDAP database: administrators can only log in using an account configured on the LDAP database and obtain privileges according to the groups and roles associated with that account. Note that if this option is selected and the LDAP server is inaccessible for any reason, administrators will not be able to log in to the Pexip Infinity web-based Administrator interface or management API. LDAP database and local database: administrators can log in using either the default local admin account or via an account configured on the LDAP database. Open ID Connect service: administrators can only log in using an account configured on the OpenID Connect provider and obtain privileges according to the groups and roles associated with that account. Note that if this option is selected and the OpenID Connect provider is inaccessible for any reason, administrators will not be able to log in to the Pexip Infinity web-based Administrator interface or management API. Open ID Connect service and local database: administrators can log in using either the default local admin account or via an account configured on the OpenID Connect provider. LDAP database, Open ID Connect service and local database: administrators can log in using the default local admin account, via an account configured on the LDAP database, or via an account configured on the OpenID connect provider. When using an LDAP database either on its own or in combination with another authentication source, you must configure the items in the LDAP configuration section. By default, Pexip Infinity checks the entered username against the Active Directory sAMAccountName attribute (as configured in the LDAP user search filter advanced setting below). Default: Local database. |
| Require client certificate |
Controls whether administrators are authenticated via a client certificate. By default, administrators log in to the Pexip Infinity Administrator interface via the standard login page, or provide an authorization header when accessing the management API. Instead, users can be required to present (via their browser) a client certificate containing their user identification details. The options are: Not required: Client certificates are not required. Administrators log in via the standard login page and provide a password which is authenticated against the selected Authentication source. Management API requests require an authorization header. Required (user identity in subject CN): administrators identify themselves via the identity contained in the subject CN (common name) of the client certificate presented by their browser. Required (user identity in subjectAltName userPrincipalName): administrators identify themselves via the identity contained in the subjectAltName userPrincipalName attribute of the client certificate presented by their browser. Default: Not required. When a client certificate is required, the standard login page is no longer presented. Administrators will not be able to access the Pexip Infinity Administrator interface or the management API if their browser does not present a valid certificate that contains a user identity which exists in the selected Authentication source. To reinstate access via the Pexip Infinity Administrator interface or management API, see Disabling certificate-based authentication. |
| Management API Oauth2 settings | |
| The settings in this section apply to management API access via OAuth only. They do not affect local, LDAP or OpenID Connect access. For more information, see Managing API access via OAuth2. | |
| LDAP configuration | |
| LDAP server address |
You must also ensure that Pexip Infinity has trusted CA certificates for the authority that signed the LDAP server’s certificate (if a TLS connection is required). We strongly recommend that you do not use an IP address. If an IP address is used, and a TLS connection is required, this will only work if the IP address is specified as the common name in the LDAP server's certificate. See Troubleshooting LDAP server connections for more information about how the system establishes a connection to the LDAP server and how to troubleshoot connection issues. |
| Allow insecure transport | By default the system will attempt to establish a secure TLS connection with the LDAP server. Select this option if you want to allow the system to fall back to a TCP connection (using SASL DIGEST-MD5). You cannot specify the LDAP server by IP address if this option is selected. |
| LDAP bind username and password |
The username |
| LDAP base DN |
The base DN (distinguished name) of the LDAP forest to query |
| OpenID Connect configuration | |
| The settings in this section apply to OpenID Connect access only. They do not affect local or LDAP access. For more information, see Managing administrator access via OIDC. | |
| Advanced LDAP configuration | |
| By default the advanced LDAP configuration settings are preconfigured for Windows Active Directory, and may also be appropriate for other LDAP databases such as OpenLDAP. | |
| Search global catalog |
Select this option to expand the scope of the search to the entire Active Directory Global Catalog instead of traditional LDAP. Note that this uses ports 3268 (TCP) and 3269 (TLS). |
| LDAP user search DN | The DN relative to the LDAP base DN to query for user records (e.g. ou=people). If blank, the LDAP base DN is used. In deployments with large user bases, you may want to configure this to optimize the LDAP user queries. |
| LDAP user filter |
The LDAP filter used to match user records in the directory. Default: (&(objectclass=person)(!(objectclass=computer))) |
| LDAP user search filter |
The LDAP filter used to find user records when given the user name. The filter must contain {username} to indicate locations into which the username is substituted. This filter is applied in conjunction with the LDAP user filter and must contain at least one substitution. If client certificate-based authentication is used, this filter usually must include 'userPrincipalName={username})' either in addition to, or instead of, the default value; for example '(|(uid={username})(sAMAccountName={username})(userPrincipalName={username}))'. To log in using an email address, you can use '(|(uid={username})(sAMAccountName={username})(mail={username}))' — note that this requires the use of LDAPS. Default: (|(uid={username})(sAMAccountName={username})) |
| LDAP group attributes |
A comma-separated list of attributes in the LDAP user record to examine for group membership information. The attribute value must contain the DN of each group the user is a member of. If no attributes are specified, or none of the specified attributes are present in the LDAP user record, an LDAP group search (using the remaining advanced configuration options below) is performed instead. Default: memberOf |
| LDAP group search DN | The DN relative to the LDAP base DN to query for group records (e.g. ou=groups) when no group attributes are present in the LDAP user record. If blank, the LDAP base DN is used. In deployments with large user bases, you may want to configure this to optimize the LDAP group queries. |
| LDAP group filter |
The LDAP filter used to match group records in the directory. Default: (|(objectclass=group)(objectclass=groupOfNames)(objectclass=groupOfUniqueNames)(objectclass=posixGroup)) |
| LDAP group membership filter |
The LDAP filter used to search for group membership of a user. The filter may contain {userdn} to indicate locations into which the user DN is substituted. The filter may contain {useruid} to indicate locations into which the user UID is substituted. This filter is applied in conjunction with the LDAP group filter and must contain at least one substitution. Default: (|(member={userdn})(uniquemember={userdn})(memberuid={useruid})) |
If authentication against an LDAP database is configured, you can save the settings only if Pexip Infinity can successfully contact the specified LDAP server.
Note that all LDAP distinguished names must be entered as per the LDAP standard (RFC 4514). LDAP configuration is case insensitive.
Certificate-based authentication
When using LDAP as an authentication source, you can configure the Pexip Infinity platform for client certificate authentication. This means that instead of logging in to the Pexip Infinity Administrator interface via the standard login page, or providing an authorization header when accessing the management API, administrators present (via their browser) a client certificate containing their user identification details. The validation of the presented certificate acts as the authentication phase and the username attributes in the certificate are used to determine which features the administrator is authorized to access.
To enable client certificate authentication, from the Require client certificate field select either of the Required...options.
Disabling certificate-based authentication
When a client certificate is required, the standard login page is no longer presented. Administrators will not be able to access the Pexip Infinity Administrator interface or the management API if their browser does not present a valid certificate that contains a user identity which exists in the selected Authentication source.
To disable client certificate authentication so that you can log in to the Pexip Infinity Administrator interface via the standard login page:
- Log in to the Management Node over SSH.
-
Run the command:
authset CBA OFF
Supporting nested security groups in Windows Active Directory
The default LDAP configuration does not support nested security groups in Windows Active Directory. For example, if group A is allowed to log in via LDAP, and if group B is a member of group A, then any user who is only a member of group B will not be allowed to log in.
To allow members of a nested Active Directory security group to log in over LDAP:
- Go to and expand the Advanced LDAP configuration section.
- Ensure that LDAP group attributes is empty (i.e. remove the default "memberOf" content).
- Change LDAP group membership filter to "(member:1.2.840.113556.1.4.1941:={userdn})"
- Select .
(This configuration uses the LDAP_MATCHING_RULE_IN_CHAIN OID. More information on this can be found at https://msdn.microsoft.com/en-us/library/aa746475%28VS.85%29.aspx.)
Configuring administrator roles
Administrator roles control the actions that administrators can perform after they have been authenticated. You create one or more administrator roles, and then
To add, edit or delete administrator roles, go to . For full details of the options that are available, see Managing administrator roles.
Configuring role mappings
LDAP role mappings are used to map the LDAP groups associated with LDAP user records to the Pexip Infinity administrator roles. You must configure a separate LDAP role mapping for each LDAP group for which you want to map one or more Pexip Infinity administrator roles.
To add, edit or delete LDAP role mappings, go to . When configuring LDAP role mappings, the options are:
Examples: configuring permissions for an AD group
These examples show how you can configure the specific actions (permissions) that all members of an AD group are allowed to perform when administering Pexip Infinity, and provide methods to filter the groups that are displayed.
The filtering options are not mandatory but they do make it easier to select the appropriate LDAP groups, and can optimize system performance.
Let's assume that you have the following set of groups already configured in Windows Active Directory:
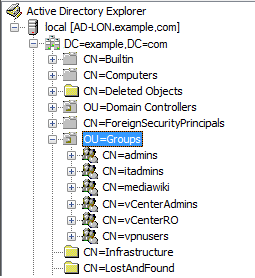
In both of the examples below you need to ensure that you have configured an LDAP authentication source () that can access your AD server, for example:

This example shows how to configure all AD users who are members of the "itadmins" group to be able to add, modify and delete VMR/conference related settings, but only be able to view other configuration aspects of Pexip Infinity (system settings, logs etc).
To make it easier to select the "itadmins" group we have specified an LDAP group search DN to limit the number of LDAP groups that are presented when configuring your LDAP roles:
- Go to where your LDAP configuration has been completed, as shown above, and open the section.
-
In this case, we want to define permissions based upon membership of specific AD groups, therefore we have configured the LDAP group search DN setting to ou=groups.
This means that when we configure the LDAP roles, the set of LDAP groups that is presented is filtered to include only those in the groups organizational unit (ou).

-
We now need to configure an administrator role () that defines the set of actions that can be performed by administrators who have been assigned that role.
Here, a "Manage Conferences" role has been created. The Chosen permissions allow an administrator to use the web interface to configure all service-related items such as VMRs, themes, gateway rules, but to only be able to view (and not modify) all other configuration.
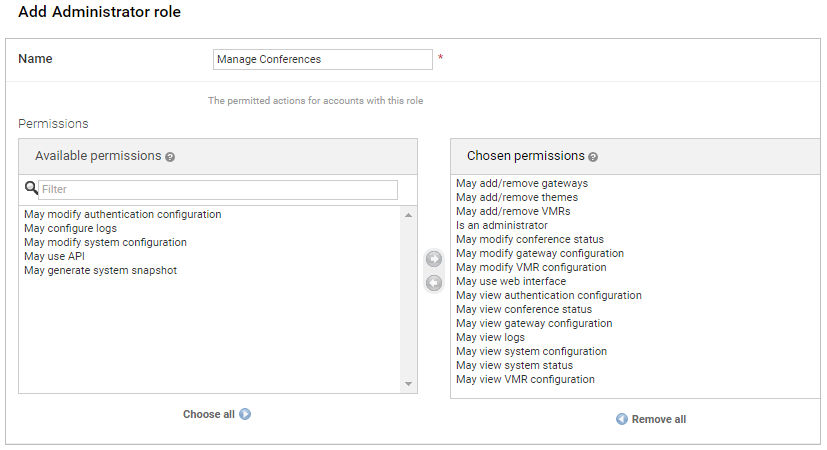
-
The final step is to associate this administrator role with an LDAP role/group ().
Here, we have configured an "IT admins - manage conferences" role with a Source of LDAP. The LDAP group DN drop-down presents a list of LDAP groups from AD. In our case this list is filtered to only show those groups in the ou=groups organizational unit (due to the LDAP group search DN configuration in step 2).
We have selected the itadmins group and associated it with the Manage Conferences role we created in step 3. (Note that you can associate the LDAP role with more than one administrator role if required.)
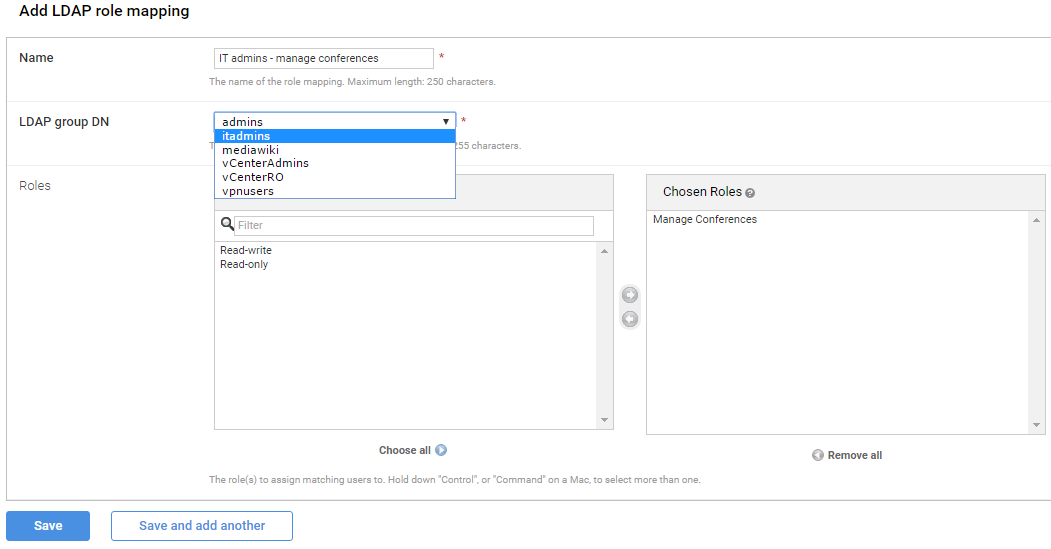
This means that AD users who are in the itadmins group can now sign in to the Pexip Infinity Administrator interface, using their AD credentials, and configure service-related settings only.
To set up different permissions for members of other AD groups, repeat steps 3 and 4 to create different administrator role and LDAP role associations.
This example is similar to the example above, but shows an alternative method of limiting the number of LDAP groups that are presented when configuring your LDAP roles.
In this case we show how to specify an LDAP group filter to limit the groups that are displayed.
- Go to where your LDAP configuration has been completed, as shown above, and open the section.
-
In this example, we are specifying a group filter so that when we configure the LDAP roles, the set of LDAP groups that is presented is filtered to only show those whose name starts with "vc".
We do this by configuring the LDAP group filter to (&(objectclass=group)(cn=vc*))

- As with the previous example, you need to ensure that you have configured an administrator role (), such as "Manage Conferences", that defines the set of actions that can be performed by administrators who have been assigned that role.
-
The final step is to associate this administrator role with an LDAP role/group ().
Here, we have configured a "vCenter Admins - Manage Conferences" role. The LDAP group DN drop-down presents a list of LDAP groups from AD. In our case this list is filtered to only show those groups whose name starts with "vc".

This means that AD users who are in the vCenterAdmins group can now sign in to the Pexip Infinity Administrator interface.
Reinstating the local admin account
If necessary you can reinstate access via the Pexip Infinity local on-box database, so that administrators can log in via the default admin account with full administrator privileges. You may need to do this if, for example, the Authentication source is configured as LDAP database only and your connectivity to the
For full instructions, see Reinstating the local admin account.