Firewall/NAT routing and addressing examples
Here are some example Pexip Infinity routing and addressing scenarios that demonstrate the various network deployment options that are available when deploying the Pexip Infinity platform:
- Public DMZ node with single NIC and externally-facing default gateway (with/without NAT)
- Public DMZ node with single NIC and three-legged firewall (with/without NAT)
- Public DMZ node with dual NICs and externally-facing default gateway (with/without NAT)
- Conferencing Node with dual NICs and routing to a video zone (with/without NAT)
For more information about how to configure static NAT, dual network interfaces and static routes, see Network routing and addressing options for Conferencing Nodes.
For specific examples that show how to deploy Proxying Edge Nodes in combination with Transcoding Conferencing Nodes, see Deployment guidelines for Proxying Edge Nodes.
Public DMZ node with single NIC and externally-facing default gateway (with/without NAT)
These types of deployment have a Conferencing Node in the public DMZ with:
- a single externally-facing interface (default gateway is out to the public internet) — this can be with or without NAT
- a static route back into the enterprise (to communicate with any private Conferencing Nodes and the Management Node)
- an internal firewall (which must not be NAT) between the enterprise nodes and the public DMZ nodes.
The static route must be applied to the Conferencing Node during its initial deployment phase (otherwise it will not be able to communicate with the Management Node and pick up its configuration).
Externally-facing interface with NAT
In this example the external firewall performs NAT:

Externally-facing interface without NAT
In this example the external firewall does not perform NAT:

Public DMZ node with single NIC and three-legged firewall (with/without NAT)
These types of deployment have a Conferencing Node in the public DMZ with:
- a single interface — this can be with or without NAT for traffic that is destined for the public internet
- a three-legged firewall that allows bi-directional routing between enterprise nodes in the LAN (any private Conferencing Nodes and the Management Node) — this must always be without NAT.
NAT applied to external traffic
In this example the firewall applies NAT to external traffic (between DMZ and internet):

NAT is not applied to external traffic
In this example the firewall does not apply NAT to external traffic (between DMZ and internet):

Public DMZ node with dual NICs and externally-facing default gateway (with/without NAT)
These types of deployment have a Conferencing Node in the public DMZ with:
- dual network interfaces:
- the primary NIC is internally-facing (eth0 must be used for all inter-node communication)
- the secondary NIC is externally-facing (eth1 must be used for signaling and media to endpoints and other video devices) — this can be with or without NAT
- the default gateway is out to the public internet (and thus is associated automatically with the secondary NIC)
- a static route back into the enterprise (to communicate with any private Conferencing Nodes and the Management Node)
- an internal firewall (which must not be NAT) between the enterprise nodes and the public DMZ nodes.
The static route must be applied to the Conferencing Node during its initial deployment phase (otherwise it will not be able to communicate with the Management Node and pick up its configuration).
Externally-facing interface with NAT
In this example the external firewall performs NAT:

Externally-facing interface without NAT
In this example the external firewall does not perform NAT:

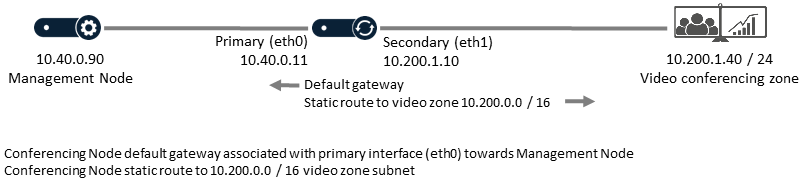
Conferencing Node with dual NICs and routing to a video zone (with/without NAT)
These types of deployment have a Conferencing Node that communicates with a dedicated video conference VLAN. It has:
- dual network interfaces:
- the primary NIC is internally-facing (eth0 must be used for all inter-node communication)
- the secondary NIC faces the video zone (eth1 must be used for signaling and media to endpoints and other video devices in the video zone) — this can be with or without NAT
- the default gateway is to the Pexip nodes (and thus is associated automatically with the primary NIC)
- a static route for traffic destined for the video zone.
Video zone routing with NAT
In this example the traffic sent to the video zone has NAT applied:

Video zone routing without NAT
In this example the traffic sent to the video zone does not have NAT applied: